In today’s rapidly evolving threat landscape, vulnerability scanning has become a critical component of any robust cybersecurity strategy. With cyber attacks growing in both frequency and sophistication, organizations need powerful tools to identify and address security weaknesses before malicious actors can exploit them. SeqOps vulnerability scanner stands at the forefront of this essential security practice, offering comprehensive detection capabilities for modern enterprise environments.
Vulnerability scanners serve as the first line of defense in identifying potential security gaps across networks, servers, applications, and cloud infrastructures. As organizations expand their digital footprint, the attack surface grows exponentially, making manual security assessments virtually impossible. This is where automated vulnerability scanning becomes indispensable – providing systematic, thorough examination of systems to uncover weaknesses that could otherwise remain hidden until exploited.
Understanding Vulnerability Scanning in Modern Security
Vulnerability scanning is the systematic process of identifying, classifying, and prioritizing security weaknesses across an organization’s IT infrastructure. Unlike penetration testing, which actively attempts to exploit vulnerabilities, scanning focuses on detection and assessment. The best vulnerability scanners not only identify known vulnerabilities but also detect misconfigurations, compliance issues, and potential security gaps that could be exploited.
The increasing complexity of modern IT environments has made vulnerability scanning more challenging and more essential than ever. With organizations utilizing a mix of on-premises infrastructure, cloud services, containers, and IoT devices, security teams need comprehensive scanning solutions that can address this diverse landscape. SeqOps has been developed specifically to meet these challenges, providing deep visibility across hybrid environments.
Why Vulnerability Scanning Matters
The importance of vulnerability scanning cannot be overstated in today’s security landscape. Recent statistics reveal that approximately 82% of cyberattacks against U.S. organizations targeted patchable external vulnerabilities. Organizations that fell victim to these attacks faced costs 54% higher than those resulting from human error. Furthermore, research indicates that up to 60% of data breaches can be attributed to poor cyber hygiene, particularly the neglect of patching known vulnerabilities.
These figures highlight a critical reality: many successful cyberattacks exploit known vulnerabilities that could have been remediated had they been identified through proper scanning. With the average time to detect a breach hovering around 277 days according to IBM research, organizations need proactive scanning tools to identify and address vulnerabilities before they can be exploited.
Key Features of SeqOps Vulnerability Scanner
SeqOps vulnerability scanner has been engineered to address the complex security challenges faced by modern organizations. Its comprehensive feature set enables security teams to identify, prioritize, and remediate vulnerabilities across diverse IT environments.
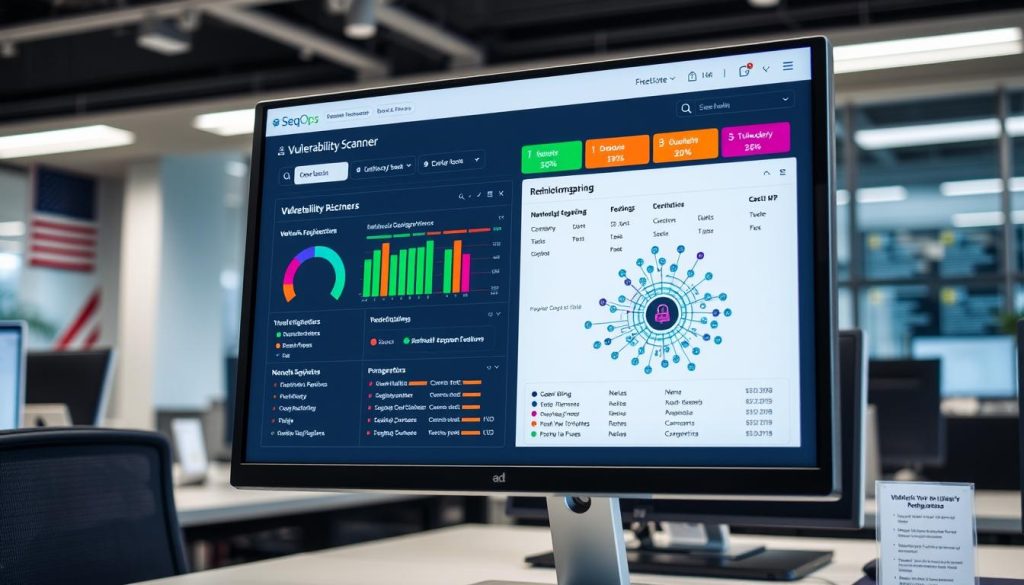
Automated Scanning Capabilities
SeqOps offers both agent-based and agentless scanning options to accommodate different organizational needs. Agent-based scanning installs lightweight software on endpoints to perform local scans and report findings to a centralized server. This approach provides deeper visibility into endpoint security posture and can operate even when devices are disconnected from the corporate network.
Agentless scanning, on the other hand, allows for non-intrusive assessment of systems without requiring software installation. This approach is particularly valuable for environments where installing agents is impractical or prohibited. SeqOps seamlessly integrates both approaches, giving security teams flexibility in how they conduct vulnerability assessments.
Agent-Based Scanning Benefits
- Deeper system inspection capabilities
- Continuous monitoring even when offline
- Reduced network traffic during scans
- More thorough assessment of endpoint security
- Ability to scan systems behind firewalls
Agentless Scanning Benefits
- No software installation required
- Minimal system resource utilization
- Rapid deployment across large environments
- Ideal for temporary or restricted systems
- Reduced maintenance overhead
Continuous Monitoring and Real-Time Detection
Traditional point-in-time vulnerability scans provide only a snapshot of security posture. SeqOps takes a more dynamic approach with continuous monitoring capabilities that detect new vulnerabilities and configuration changes in real-time. This approach dramatically reduces the window of opportunity for attackers to exploit newly discovered vulnerabilities.
The system employs advanced anomaly detection algorithms to identify unusual patterns that may indicate security issues or active exploitation attempts. When potential threats are detected, SeqOps can automatically trigger alerts and initiate response workflows to contain and remediate the issue before it can be exploited.

Threat Intelligence Integration
SeqOps incorporates comprehensive threat intelligence feeds to enhance vulnerability detection and prioritization. By correlating identified vulnerabilities with real-world exploit data, the system can accurately determine which vulnerabilities pose the greatest risk to an organization’s specific environment.
This intelligence-driven approach helps security teams focus their remediation efforts on the vulnerabilities most likely to be exploited, rather than attempting to address all identified issues simultaneously. The threat intelligence database is continuously updated to reflect emerging threats and zero-day vulnerabilities, ensuring organizations remain protected against the latest attack vectors.
Comprehensive Asset Coverage
One of the standout features of SeqOps is its ability to scan diverse assets across hybrid environments. The scanner provides comprehensive coverage for:
Server Infrastructure
Complete scanning for Windows servers, Linux distributions, and virtualized server environments to identify OS-level vulnerabilities, misconfigurations, and security gaps.
Cloud Environments
Specialized scanning for AWS, Azure, and GCP deployments, including infrastructure-as-code templates, cloud storage configurations, and identity management settings.
Applications & Databases
Deep inspection of web applications, APIs, and database systems to identify SQL injection vulnerabilities, cross-site scripting opportunities, and other application-level weaknesses.
SeqOps' 4-Step Vulnerability Management Process
SeqOps implements a structured, four-phase approach to vulnerability management that ensures comprehensive protection for organizations. This methodology addresses the entire vulnerability lifecycle from initial discovery through remediation and verification.

1. Discovery Phase
The discovery phase forms the foundation of effective vulnerability management. During this initial stage, SeqOps conducts comprehensive asset discovery to identify and catalog all elements within an organization’s digital footprint. This includes network infrastructure, software applications, physical devices, endpoints, cloud resources, and data repositories.
Asset discovery is critical because organizations cannot protect what they don’t know exists. Many security breaches exploit forgotten systems or shadow IT resources that aren’t included in regular security assessments. SeqOps employs multiple discovery methods to ensure complete visibility:
- Network scanning to identify connected devices and open ports
- API integration with cloud service providers to discover cloud assets
- Integration with configuration management databases
- Passive network monitoring to detect transient devices
- Agent-based discovery for detailed endpoint inventory
The result is a comprehensive asset inventory that serves as the foundation for subsequent vulnerability scanning activities. This inventory is continuously updated to reflect changes in the environment, ensuring no assets escape security scrutiny.
2. Vulnerability Scanning
With a complete asset inventory established, SeqOps proceeds to the vulnerability scanning phase. This involves systematically examining each asset for security weaknesses that could potentially be exploited by attackers. The scanning process is highly configurable, allowing organizations to balance thoroughness with performance impact.

SeqOps vulnerability scanning capabilities include:
Network Vulnerability Detection
- Open port identification and service enumeration
- Network protocol vulnerability assessment
- Firewall and router configuration analysis
- Network segmentation verification
- Wireless network security assessment
System Vulnerability Detection
- Operating system patch verification
- Software version and update checking
- Secure configuration assessment
- Authentication and access control review
- Privilege escalation vulnerability detection
The scanning process employs multiple techniques to minimize false positives while ensuring comprehensive coverage. Each identified vulnerability is assigned a severity rating based on the Common Vulnerability Scoring System (CVSS), which considers factors such as exploit complexity, required privileges, and potential impact.
3. Detection & Management
Once vulnerabilities are identified, SeqOps enters the detection and management phase. This involves analyzing the discovered vulnerabilities, prioritizing them based on risk, and developing remediation strategies. The system combines threat intelligence with environmental context to determine which vulnerabilities pose the greatest risk to the specific organization.
SeqOps’ advanced risk prioritization engine considers multiple factors:
- Vulnerability severity based on CVSS scoring
- Existence of known exploits in the wild
- Asset criticality and business impact
- Network exposure and accessibility
- Compensating controls that may mitigate risk
This contextual approach to vulnerability management ensures that remediation efforts focus on the issues that matter most. According to IBM research, organizations using advanced vulnerability management solutions like SeqOps can reduce their time to detect and respond from the industry average of 277 days to just minutes, dramatically reducing the window of opportunity for attackers.
4. Reporting & Remediation
The final phase of the process involves comprehensive reporting and remediation guidance. SeqOps generates detailed reports tailored to different stakeholders, from executive summaries for leadership to technical details for security teams. These reports provide clear visibility into the organization’s security posture and track remediation progress over time.

For each identified vulnerability, SeqOps provides specific remediation guidance, including:
- Step-by-step instructions for addressing the vulnerability
- Links to relevant patches or updates
- Configuration changes to implement
- Verification steps to confirm successful remediation
- Potential impact assessment for remediation actions
The system also supports integration with IT service management platforms to automate the creation of remediation tickets and track their progress. This integration streamlines the remediation workflow and ensures that vulnerabilities don’t fall through the cracks.
Addressing the Impact of Unpatched Vulnerabilities
Unpatched vulnerabilities represent one of the most significant cybersecurity risks facing organizations today. Despite their known status, these vulnerabilities continue to be successfully exploited by attackers due to delays in patching and remediation efforts.
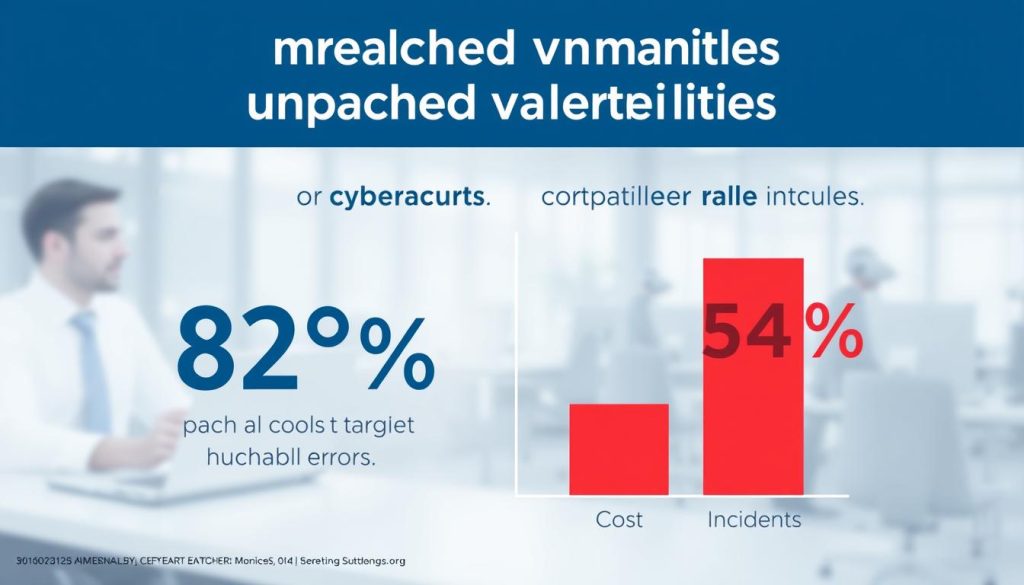
The Cost of Delayed Patching
Recent data from the first quarter of 2022 highlights that approximately 82% of cyberattacks against U.S. organizations targeted patchable external vulnerabilities. The financial repercussions of these attacks were substantial, with affected organizations experiencing costs that were 54% higher compared to incidents stemming from human error.
Expanding the scope, broader research indicates that up to 60% of data breaches can be attributed to poor cyber hygiene, particularly the neglect of patching vulnerabilities. Despite organizations’ efforts to scan for vulnerabilities, the challenge often lies in inadequate patch management solutions. Factors such as concerns about disrupting business operations and non-compliance with data security legislation contribute to delays in implementing security patches.
SeqOps' Approach to Patch Management
SeqOps addresses the challenges of patch management through a comprehensive approach that balances security needs with operational considerations. The system provides:
- Patch impact analysis to assess potential operational disruptions
- Scheduling capabilities for implementing patches during maintenance windows
- Rollback procedures in case patches cause unexpected issues
- Verification testing to confirm patch effectiveness
- Compliance tracking to ensure regulatory requirements are met
This structured approach to patch management helps organizations overcome the common barriers to timely patching, reducing the window of vulnerability and improving overall security posture.
Advanced Security Solutions from SeqOps
Beyond core vulnerability scanning, SeqOps offers a comprehensive suite of security solutions designed to protect organizations across their entire IT landscape. These integrated capabilities provide defense-in-depth protection against evolving threats.

Cloud Security Solutions
As organizations increasingly migrate to cloud environments, securing these deployments becomes critical. SeqOps provides specialized security solutions for major cloud platforms including AWS, Azure, and GCP. These solutions address the unique security challenges of cloud computing, including:
- Cloud configuration security assessment
- Identity and access management review
- Storage bucket and object security verification
- Serverless function security analysis
- Container security assessment
SeqOps also provides Infrastructure as Code (IaC) scanning capabilities, allowing organizations to identify security issues in their cloud templates before deployment. This shift-left approach to security helps prevent vulnerabilities from being introduced in the first place.
Server Protection
Servers often contain an organization’s most critical data and applications, making them prime targets for attackers. SeqOps provides comprehensive protection for server environments, with specialized capabilities for Windows Server and various Linux distributions.

Server protection features include:
- Operating system vulnerability assessment
- Application and service security scanning
- Configuration hardening verification
- Privilege escalation vulnerability detection
- Network service security assessment
The system also provides physical security recommendations for server environments, addressing an often-overlooked aspect of comprehensive security.
Penetration Testing
While vulnerability scanning identifies potential security weaknesses, penetration testing attempts to exploit these vulnerabilities to determine their real-world impact. SeqOps includes advanced penetration testing capabilities that simulate real-world attack scenarios to validate the effectiveness of security controls.
The penetration testing module follows a structured methodology:
- Reconnaissance to gather information about the target environment
- Vulnerability scanning to identify potential entry points
- Exploitation attempts to validate vulnerabilities
- Post-exploitation activities to assess potential damage
- Reporting and remediation recommendations
This approach provides organizations with a realistic assessment of their security posture and helps identify vulnerabilities that might be missed by automated scanning alone.
Load Testing
Security isn’t just about preventing unauthorized access; it’s also about ensuring system availability. SeqOps includes load testing capabilities that assess how systems perform under stress, helping organizations identify performance bottlenecks that could lead to denial of service.
Load testing features include:
- Scalable traffic generation to simulate user loads
- Performance metrics collection and analysis
- Bottleneck identification and remediation recommendations
- Capacity planning guidance
- Stress testing to identify breaking points
By combining security testing with performance testing, SeqOps provides a more comprehensive assessment of overall system resilience.
Compliance and Security: A Unified Approach
For many organizations, compliance with regulatory requirements is a primary driver for security initiatives. SeqOps takes a unified approach to compliance and security, recognizing that effective security controls contribute to compliance, while compliance requirements can guide security priorities.
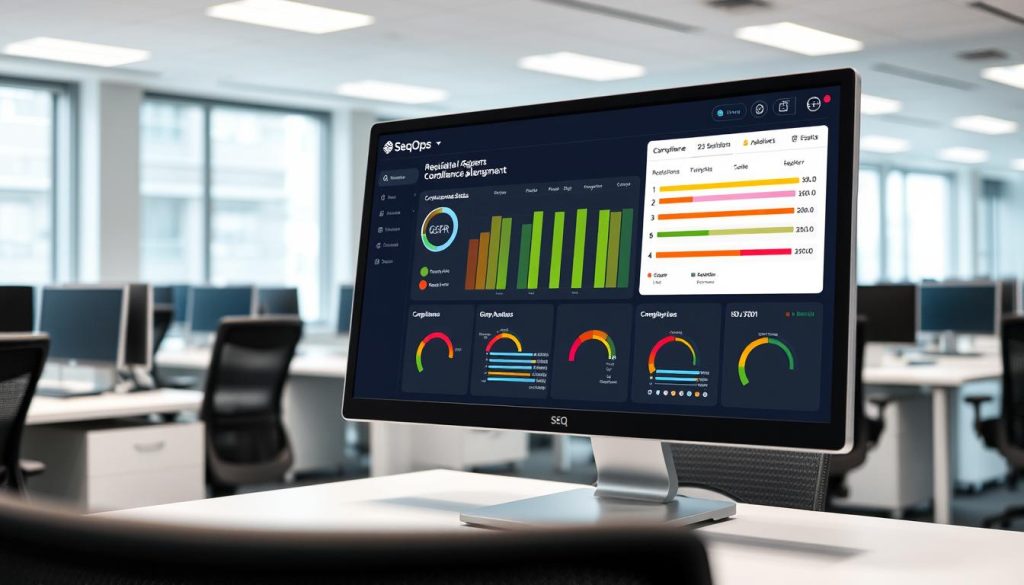
Comprehensive Compliance Coverage
SeqOps provides built-in support for numerous regulatory frameworks and industry standards, including:
Industry Regulations
- GDPR for data protection
- HIPAA for healthcare information
- PCI DSS for payment card data
- GLBA for financial institutions
- CCPA for consumer privacy
Security Standards
- ISO 27001/27002
- NIST Cybersecurity Framework
- CIS Controls
- SOC 2
- COBIT
Industry-Specific Standards
- NERC CIP for energy
- FISMA for federal systems
- CMMC for defense contractors
- DISA STIGs for defense
- FDA requirements for medical devices
For each supported framework, SeqOps maps vulnerability findings to specific compliance requirements, helping organizations understand how security issues impact their compliance posture. This mapping also guides remediation priorities, ensuring that the most compliance-critical vulnerabilities are addressed first.
Automated Compliance Reporting
SeqOps streamlines compliance reporting with automated report generation tailored to specific regulatory frameworks. These reports provide comprehensive evidence of security controls and vulnerability management activities, simplifying the audit process and reducing the administrative burden of compliance.
The system maintains detailed audit trails of all scanning and remediation activities, providing the documentation needed to demonstrate due diligence to auditors and regulators. This historical record also enables trend analysis to show improvement in security posture over time.
The Case for Proactive Cybersecurity
In today’s threat landscape, reactive security approaches are increasingly inadequate. By the time a breach is detected, significant damage has often already occurred. SeqOps promotes a proactive approach to cybersecurity that identifies and addresses vulnerabilities before they can be exploited.

The Economics of Prevention
The financial case for proactive security is compelling. According to industry research, the average cost of a data breach now exceeds $4.35 million, while the cost of implementing effective vulnerability management is a fraction of that amount. By identifying and addressing vulnerabilities before they can be exploited, organizations can avoid the substantial costs associated with breach response, customer notification, regulatory penalties, and reputational damage.
Beyond direct financial benefits, proactive security also contributes to business continuity by preventing the operational disruptions that often accompany security incidents. This approach allows organizations to maintain customer trust and focus on their core business objectives rather than crisis management.
Building a Security-First Culture
Effective security requires more than just technology; it requires a security-first organizational culture. SeqOps supports this cultural transformation by providing visibility into security posture across the organization and engaging stakeholders at all levels in the security process.
The system’s intuitive dashboards and reports make security accessible to non-technical stakeholders, helping them understand security risks in business terms. This broader engagement helps build support for security initiatives and ensures that security considerations are integrated into business decisions from the outset.
Conclusion: Comprehensive Protection in an Evolving Threat Landscape
As cyber threats continue to evolve in sophistication and impact, organizations need comprehensive security solutions that can adapt to changing attack vectors. SeqOps vulnerability scanner provides the foundation for effective security by identifying vulnerabilities across diverse IT environments and guiding prioritized remediation efforts.

By combining automated scanning with threat intelligence, contextual risk assessment, and comprehensive remediation guidance, SeqOps enables organizations to stay ahead of potential threats. The system’s integrated approach to security and compliance ensures that security efforts are aligned with business requirements and regulatory obligations.
In an era where cyber attacks can have devastating consequences for organizations of all sizes, proactive vulnerability management has become an essential component of business strategy. SeqOps provides the tools and insights needed to implement this proactive approach, helping organizations protect their critical assets and maintain the trust of their customers and partners.
As the threat landscape continues to evolve, SeqOps remains committed to innovation, continuously enhancing its capabilities to address emerging threats and security challenges. This commitment to ongoing improvement ensures that organizations using SeqOps will maintain a strong security posture even as attack techniques become more sophisticated.






