

Cloud-Based Vulnerability Management
Continuous Vulnerability Security and Risk Visibility Across Servers
SeqOps is a SaaS platform that provides continuous cloud-based vulnerability management across AWS, Azure, and Google Cloud. Automated scanning identifies misconfigurations and exposure risks in real time, while built-in prioritization and remediation workflows help teams reduce risk across multi-cloud environments.
What Is Cloud-Based Vulnerability Management?
Cloud-based vulnerability management is the continuous process of identifying, prioritizing, and remediating security risks across cloud environments. Unlike traditional audits, it provides real-time visibility into misconfigurations, exposed assets, and compliance gaps across multi-cloud infrastructure.
Why Cloud Security Infrastructure Resilience Matters
Moving to the cloud gives you an unmatched level of scalability, but it also makes multi-cloud security environments much more vulnerable to attacks that are often hard to see. When everything is in the cloud, perimeter-based security isn’t enough anymore. A single misconfigured bucket or an API key with too many permissions can make your whole infrastructure available to the public internet in seconds, which can lead to huge data leaks, security problems, and not following the rules.
Misconfigurations and excessive permissions remain one of the most common causes of cloud security incidents. Without continuous visibility, a single configuration change can expose critical resources within minutes.
Continuous Cloud-Based Vulnerability Management with SeqOps
It’s no longer enough to only do periodic manual audits of cloud environments. People can’t keep up with how quickly cloud infrastructure changes. SeqOps offers automation in cloud security, which means that your multi-cloud security environment can always find new threats and respond to them right away. This is how it works:
- Continuous Discovery & Inventory: SeqOps automatically detects new cloud workloads, storage buckets, and serverless functions the moment they appear, ensuring no “shadow IT” or forgotten assets are left unmonitored across multi-cloud solutions.
- Real-Time Misconfiguration Scanning: Automated scanning detects high-risk configuration changes such as publicly exposed services or overly permissive identities shortly after they occur, helping teams respond before risks escalate.
- Intelligent Prioritization: By correlating threat signals with your specific business context, our system flags the most critical risks first, reducing “alert fatigue” and allowing your team to focus on what matters most.
- Proactive Remediation: Stay compliant and secure with automated playbooks that can instantly isolate compromised containers or apply corrective patches without manual intervention.
Automation not only reduces operational overhead but also ensures your cloud-native assets are protected 24/7, providing a robust defense that scales at the speed of your business.
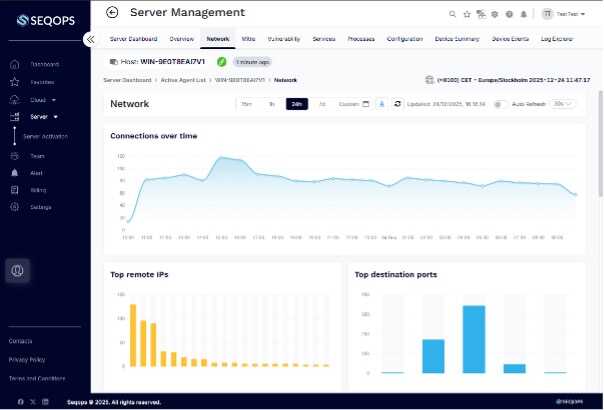
Customize Your Cloud Security Solutions with Real-Time Monitoring
SeqOps’ ongoing protection against cloud-native threats in complicated multi-cloud security settings will make your defence more effective. We know that security measures that don’t change aren’t enough in today’s digital world. With our Cloud Vulnerability Assessment and Penetration Testing (VAPT) services, which are based on tried-and-true cloud-based vulnerability management methods, you can keep an eye on your whole cloud ecosystem at all times using standardised tools, well-defined processes, and enterprise security standards.
- Beyond Periodic Testing: Our model of SeqOps enriches vulnerability findings with attack-path context and optional validation, helping teams understand how risks could be exploited and which issues to address first.
- Instant Risk Detection: SeqOps spots anomalous behavior and lateral movement within your virtual networks, catching problems before they escalate into major data breaches caused by security misconfigurations or hidden security vulnerabilities.
- Context-Aware Safety: We tailor our monitoring to your cloud architecture and use multi-cloud orchestration principles to keep your most important workloads safe 24/7, in line with compliance requirements, and without affecting performance.
How to Scan Your Multi-Cloud Environment with Multi-Cloud Security
Add Your Cloud Accounts
Connect your AWS, Azure, and Google Cloud accounts to enable multi-cloud security solutions and start cloud based vulnerability management across your environments.
Start Fixing Issues
Identify and prioritize security misconfigurations and security misconfiguration vulnerability findings based on business impact using vulnerability management cloud workflows.
Automated Cloud Security
Automatically discover and scan new cloud assets using multi-cloud orchestration, helping teams manage multi-cloud cost and security through continuous multi-cloud security monitoring.
SeqOps Multi-Cloud Security Solutions
SeqOps delivers cloud based vulnerability management to secure AWS, Azure, and Google Cloud from a single platform. Continuous detection identifies security misconfigurations, exposed assets, and security misconfiguration vulnerability issues as infrastructure changes, supporting consistent multi-cloud security without relying on periodic audits or disconnected tools.
Benefits of SeqOps Multi-Cloud Security Solutions
Automated Vulnerability Scanning
SeqOps continuously runs cloud based vulnerability management to detect security misconfigurations and security misconfiguration vulnerability issues as infrastructure changes. Findings are automatically prioritized to support faster remediation across multi-cloud security environments.
Reduced Operational Overhead
Automated vulnerability management cloud workflows remove repetitive manual effort. Centralized visibility helps teams maintain strong multi-cloud security solutions while focusing on scaling applications and infrastructure.
Regulatory and Policy Alignment
Built-in checks continuously evaluate environments against common regulatory and policy requirements. Ongoing monitoring reduces configuration-related risk and supports consistent multi-cloud security across providers.
Cloud Infrastructure Hardening
SeqOps identifies insecure configurations and exposure risks across cloud resources. Continuous monitoring and guided fixes improve resilience by addressing security misconfigurations as environments evolve.
Scalable Multi-Cloud Architecture
Designed for modern cloud environments, SeqOps supports multi-cloud solutions across public, private, and hybrid infrastructure. Protection scales automatically as cloud usage grows.
Risk Context and Prioritization
Detected issues are analyzed with configuration context to highlight impact and exposure. This structured approach strengthens vulnerability management cloud by helping teams focus on the most critical risks first.


Six Simple Steps to Secure Multi-Cloud Environments with SeqOps

Connect Your Cloud Accounts
Securely connect AWS, Azure, and Google Cloud accounts using read-only access to enable multi-cloud security solutions and centralized visibility.

Automatic Asset Discovery
SeqOps automatically discovers cloud resources across providers as they are created or updated, supporting consistent multi-cloud orchestration and visibility.

Continuous Risk Detection
Resources are continuously analyzed to detect security misconfigurations and security misconfiguration vulnerability issues as environments change.

Intelligent Risk Prioritization
Findings are prioritized based on exposure and potential impact, helping teams focus remediation efforts using structured vulnerability management cloud workflows.

Guided Remediation & Reporting
Clear remediation guidance and exportable reports support faster fixes and audit readiness through cloud based vulnerability management.

Ongoing Security Posture Monitoring
Continuous monitoring maintains consistent multi-cloud security across environments, helping teams manage multi-cloud cost and security as workloads scale.
Secure Your Multi-Cloud Security Environment with Advanced Automation & Reporting
SeqOps doesn’t just protect; it empowers. Its comprehensive reporting transforms complex cloud telemetry into actionable insights, supporting cloud-based vulnerability management and helping administrators:
- Identify recurring misconfigurations across multi-cloud security environments
- Isolate security gaps across multi-cloud environments using standardized detection tools
- Develop actionable strategies for cloud-native defense aligned with enterprise security standards
For example, SeqOps will flag your cloud storage buckets if someone tries to access them without permission. It will also explain why this is happening and suggest ways to fix it automatically. This level of insight makes vulnerability management cloud programs stronger, helps people make better decisions, and stops future breaches by making security processes clear and easy to check.
Tailored Public vs. Private Cloud Security for Multi-Cloud Solutions
When it comes to keeping the cloud safe, there is no one-size-fits-all solution. SeqOps offers multi-cloud solutions for both public and private clouds that are customised to meet your specific infrastructure needs, compliance goals, and security misconfiguration definition frameworks. These solutions are backed by proven tools, clear processes, and enterprise-grade security standards.
| Factor | Public Cloud Security | Private Cloud Security |
|---|---|---|
| Scalability | High, grows instantly with your needs | Limited by physical hardware/on-prem resources |
| Cost | Flexible pay-as-you-go model | Upfront capital investment |
| Control | Shared responsibility with provider | Full control over internal configurations |
| Business Fit | Ideal for startups & remote-first teams | Better for strict data sovereignty needs |

Pricing Plans for SeqOps Server Security
SeqOps doesn’t just protect; it empowers. Its comprehensive reporting transforms raw data into actionable insights, helping administrators:
Basic
Per month price:
30 Days
Scanning Frequency
What you get:
- Monthly reporting
- Vulnerability detection
Advanced
Per month price:
30 Days
Scanning Frequency
What you get:
- Monthly reporting
- Vulnerability detection
Enterprise
Custom Quote
Full security and tailored to your needs
30 Days
Scanning Frequency
What you get:
- Managed Detection
- GDPR and NIST Reporting
- Threat alerts and attempt block
- Daily scans and reporting
Related Posts
- /
Data breaches now cost businesses an average of $4.45 million per incident, a record high according to the...
- /
Did you know that over 60% of data breaches result from unpatched security flaws that organizations knew about...
- /
A staggering 68% of businesses experience a significant security incident within their first year of operation. This alarming...
Frequently Asked Questions
What is a cloud security audit?
A cloud security audit evaluates cloud environments to identify risks, misconfigurations, and compliance gaps. SeqOps supports this process through continuous monitoring and reporting across public, private, and multi-cloud environments.
How often should cloud security reviews be performed?
In dynamic cloud environments, security assessment should be continuous. Automated monitoring combined with periodic expert review helps maintain visibility as infrastructure and threats evolve.
Can SeqOps work with our cloud architects on remediation?
Yes. SeqOps can integrate with internal teams to support remediation workflows, compliance mapping, and governance practices across multi-cloud environments.
Why do I need cloud vulnerability management?
Cloud environments change constantly, and misconfigurations are a common source of security risk. Continuous vulnerability management helps identify exposure early, prioritize remediation, and maintain compliance across cloud providers.
What kind of support does SeqOps provide?
SeqOps provides onboarding support, continuous monitoring, alerting, and guided remediation. Expert assistance is available when deeper validation or remediation guidance is needed.

Ready to Improve How You Manage Security?
Discover how the SeqOps platform helps your business work more efficiently while keeping your organization secure now and as you grow.



