

Security Audit for Compliance and Infrastructure Protection
Continuous Vulnerability Audit for Cloud Environments
SeqOps enables a continuous security audit through an automated, product-led platform designed to identify risk and maintain visibility across environments. This approach supports an ongoing vulnerability audit that helps teams understand exposure and strengthen overall risk visibility without relying on service-based audit models.
Security Audit for Infrastructure Risk Visibility
SeqOps enables an automated security audit that helps teams identify and understand risk across their infrastructure before issues escalate. The platform analyzes configurations, access paths, and exposure points to provide continuous insight across environments without relying on manual or expert-led audits.
The SeqOps platform helps teams:
- Identify Vulnerability Gaps: Continuous vulnerability audit capabilities surface weaknesses across systems, applications, and configurations using automated analysis.
- Maintain Compliance Readiness: Compliance alignment is supported through consistent visibility into configurations and risk signals.
- Prioritize Risk Clearly: Findings are organized by impact and exposure, helping teams focus remediation efforts where it matters most.
- Strengthen Operational Resilience: Ongoing visibility supports stronger overall risk visibility and business continuity as environments evolve.
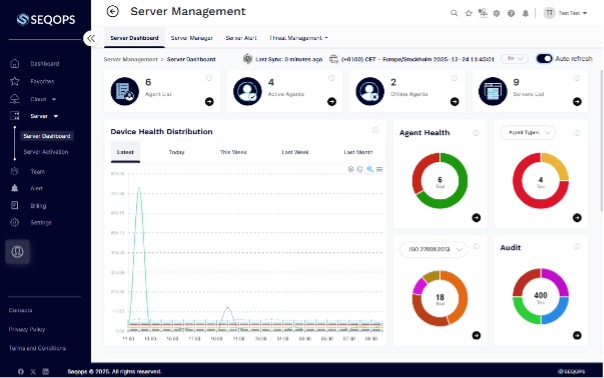
Continuous Security Audit Services for Infrastructure Stability
SeqOps delivers automated audit capabilities that help teams maintain continuous visibility into infrastructure risk as environments change. The platform continuously monitors changes, configurations, and exposure points to support proactive overall risk visibility without relying on managed service models.
Through centralized analytics and automated checks, SeqOps provides scalable audit automation that adapts as environments evolve. This product-led approach helps organizations stay aligned with security objectives, reduce operational friction, and maintain consistent protection as infrastructure grows.
How to Run a Cloud Security Audit Infrastructure with SeqOps
Add Your Cloud Environment
Connect your infrastructure to initiate a cloud security audit infrastructure scan. SeqOps automatically discovers assets and configurations to establish baseline visibility.
Prioritize Security Findings
Identified risks are analyzed based on impact and exposure, helping teams focus remediation efforts where security gaps matter most.
Automate Continuous Monitoring
SeqOps continuously monitors changes across infrastructure, ensuring ongoing visibility and maintaining consistent overall risk visibility over time.
Cybersecurity Audit Services for Modern Cloud Environments
Our proactive approach helps organizations maintain visibility across their infrastructure and stay ahead of evolving risks. SeqOps continuously analyzes configurations, access paths, and exposure points to provide always-on audit visibility.
Understand your risk posture through structured insights and actionable findings that strengthen defenses and support long-term security confidence.
Benefits of SeqOps Security Audit & Review
Comprehensive Security Audit
SeqOps runs a continuous security audit to surface misconfigurations and exposure points across infrastructure before they escalate into real threats.
Regulation-Ready Compliance Visibility
Built-in checks map controls to compliance requirements and highlight gaps that need attention.
Stronger Infrastructure Protection
A focused cloud security audit infrastructure approach helps teams identify weaknesses across environments and maintain consistent protection.
Actionable Vulnerability Audit
SeqOps performs a structured vulnerability audit that prioritizes findings based on risk and impact, not just raw scan results.
Continuous Audit Visibility
Automated audit workflows provide ongoing visibility into configuration and risk changes as configurations and assets evolve.
Scalable Audit Automation Platform
SeqOps delivers a product-led security audit platform that scales with infrastructure growth without added operational complexity.
Six Easy Steps to a Safer Business with SeqOps Security Audit & Review
Get Started
Begin your security audit by connecting your environment to SeqOps. The platform initiates automated discovery to build visibility into assets, configurations, and exposure points.
Define Audit Scope
SeqOps structures the cybersecurity audit service by mapping systems, access paths, and controls to ensure coverage aligns with real infrastructure risk.
Provide Context
Environment signals and configuration data enrich the vulnerability audit, helping reflect real-world conditions and meaningful security exposure.
Run Continuous Analysis
SeqOps performs ongoing analysis across infrastructure as part of a cloud security audit infrastructure, identifying weaknesses as changes occur.
Review Clear Findings
Results from audit and assessment services are presented in a clear, structured format that highlights impact, severity, and remediation priority.
Maintain Ongoing Security
With continuous visibility and tracking, the platform helps teams reduce risk over time and maintain stronger overall risk visibility.
Continuous Security Audit Services with Proactive Audits
Security risks evolve constantly. SeqOps delivers continuous audit automation that shifts teams from reactive checks to proactive, ongoing visibility.
- In-Depth Security Audit: SeqOps analyzes infrastructure components, configurations, and access paths to surface risk across environments.
- Compliance-Ready Reviews: Built-in audit automation helps track alignment with security standards and reduce compliance gaps.
- Complete Infrastructure Coverage: A structured cloud security audit infrastructure approach maintains visibility as assets and configurations change.
- Future-Ready Posture: Ongoing audit and assessment services help teams track improvements and maintain long-term security confidence.
Security Audit Services to Safeguard Your Business
SeqOps delivers a product-led security platform that combines automated analysis with continuous visibility, helping teams strengthen overall risk visibility and align controls with business goals.
- Automated Security Validation: SeqOps continuously evaluates configurations and controls through structured audit automation, highlighting gaps without manual effort.
- Scalable Audit Coverage: Built-in cybersecurity audit services support ongoing reviews across infrastructure as environments change.
- Operational Focus: Centralized findings and tracking reduce overhead, allowing teams to focus on improvement and resilience.
- Growth-Ready Compliance: Continuous audit automation helps maintain compliance alignment as environments scale. while scaling securely.
Pricing Plans for SeqOps Server Security
SeqOps doesn’t just protect; it empowers. Its comprehensive reporting transforms raw data into actionable insights, helping administrators:
Basic
Per month price:
30 Days
Scanning Frequency
What you get:
- Monthly reporting
- Vulnerability detection
Advanced
Per month price:
30 Days
Scanning Frequency
What you get:
- Monthly reporting
- Vulnerability detection
Enterprise
Custom Quote
Full security and tailored to your needs
30 Days
Scanning Frequency
What you get:
- Managed Detection
- GDPR and NIST Reporting
- Threat alerts and attempt block
- Daily scans and reporting
Related Posts
- /
Data breaches now cost businesses an average of $4.45 million per incident, a record high according to the...
- /
Did you know that over 60% of data breaches result from unpatched security flaws that organizations knew about...
- /
A staggering 68% of businesses experience a significant security incident within their first year of operation. This alarming...
Frequently Asked Questions
What is an IT security audit?
An IT security audit is a structured security audit process that evaluates configurations, access controls, and exposure points across infrastructure. SeqOps runs this audit continuously to help teams identify gaps, validate controls, and maintain visibility as systems change.
Why should I conduct security reviews or audits?
Security environments evolve constantly. Continuous audit automation helps identify misconfigurations, policy gaps, and emerging risks early, policy gaps, and emerging risks early, reducing exposure and supporting stronger long-term overall risk visibility.
How often should I conduct security reviews or audits?
Instead of periodic checks, SeqOps supports continuous audit workflows through a product-led platform. This approach ensures reviews stay up to date as assets, configurations, and access patterns change without waiting for scheduled audits.
I have done a security review. Does that mean I am safe now?
A one-time review provides a snapshot in time. Ongoing audit automation is needed to track changes and detect new risks as environments evolve, helping teams stay aligned with real-world threat conditions.
How long does a security audit or review take?
Traditional audits run for a fixed duration, but SeqOps delivers continuous analysis through its cloud security audit infrastructure. As new changes occur, findings are updated automatically without restarting the process.
What is the price of Security Audit & Review?
Pricing is based on environment size and coverage. SeqOps is a subscription-based security platform that scales with infrastructure, allowing teams to start small and expand coverage as environments grow.
Ready to Improve How You Manage Security?
Discover how the SeqOps platform helps your business work more efficiently while keeping your organization secure now and as you grow.



