

Automated Vulnerability Management Security for Server Environments
Continuous Vulnerability Security and Risk Visibility Across Servers
SeqOps is a product-led vulnerability management security platform designed to help teams continuously identify, prioritize, and track security vulnerability exposure across server environments. The platform uses automated scanning and structured workflows to maintain strong vulnerability security without manual effort or external services.
Vulnerability Management Security Built for Modern Server Infrastructure
Servers support critical workloads and sensitive data, making vulnerability management cyber security essential for reducing exposure over time. Manual scans and point-in-time assessments often miss changes, leaving environments vulnerable between reviews.
SeqOps delivers security vulnerability management solutions through a SaaS-first approach. The platform continuously scans servers to identify known CVE vulnerability exposure and configuration risks, ensuring consistent visibility as environments evolve.
Findings are automatically prioritized, helping teams move faster from detection to vulnerability remediation using a clear and repeatable workflow.
Vulnerability Management Security with Automated Protection Workflow
This approach is built on a product-led vulnerability management security platform that continuously identifies and reduces server risk using two automated capabilities:
- Automated Vulnerability Scanning: Continuously scans servers to detect CVE vulnerability exposure and configuration risks that impact security posture.
- Risk-Based Prioritization: Automatically ranks findings based on severity, exposure, and remediation impact to support faster vulnerability remediation.
This workflow ensures consistent vulnerability management security without manual intervention or service dependency.
Vulnerability Management Security That Adapts to Your Server Environment
SeqOps applies vulnerability management security across your server infrastructure through continuous monitoring and automated detection, strengthening overall vulnerability security. The platform adjusts scanning and prioritization as environments change, maintaining visibility into security risks over time.
Automated scans and structured remediation workflows help reduce exposure, track remediation progress, and support ongoing security vulnerability remediation through a single, unified open source vulnerability management aligned system.
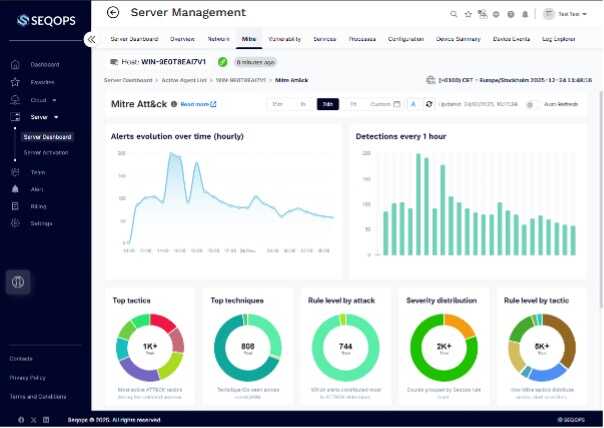
Automated Vulnerability Management Security with Continuous Monitoring
To keep your server safe, you need to be able to see and control it all the time. SeqOps offers a product-led vulnerability management security platform that keeps an eye on servers all the time, finds risks, and improves overall vulnerability security through automated workflows that follow security analyst meta requirements without the need for manual intervention.
The platform continuously evaluates server configurations and known CVE vulnerability exposure, helping reduce security gaps and maintain long-term protection through consistent vulnerability management security.
24/7 Vulnerability Management Security Across Server Infrastructure: SeqOps keeps an eye on server environments all the time to keep vulnerability management security in place as the infrastructure changes. Automated detection and prioritization give teams real-time information about security risks, so they can act quickly to lower the chances of downtime or exposure.
Scalable Vulnerability Management Security with Automated Risk Reduction: SeqOps makes vulnerability management security stronger by always keeping an eye on configuration drift and the status of vulnerability remediation. As environments grow, automated monitoring and structured workflows help keep security strong, lower the attack surface, and support ongoing security vulnerability remediation all from one platform.
How Vulnerability Management Security Works with SeqOps
Install and Configure to Start Scanning
Set up the agent, give it the permissions it needs, and connect through API access. SeqOps does an initial scan to set up a baseline and register the server environment. Once connected, the platform starts scanning automatically to find security issues without any work on your part.
Start Fixing Issues
SeqOps safely processes scan data to find and sort security issues. Issues are ranked based on how risky they are and how much damage they could cause. This makes it easy to see what needs to be fixed right away and speeds up the process of fixing them through structured workflows.
Server
SeqOps finds and scans servers automatically by keeping an eye on them all the time. We check our findings against trusted sources of vulnerability intelligence, and we make sure that our recommended actions are in line with industry security standards so that we can consistently lower risk.
SeqOps Vulnerability Management Security
Our product-led platform continuously identifies and reduces server security risk, helping protect operations, data, and system reliability through automated vulnerability management security.
Discover how SeqOps delivers consistent visibility into security findings and remediation progress using an automated vulnerability management security workflow.
Key Benefits of SeqOps Vulnerability Management Security
Automated Vulnerability Scanning
Continuous scanning identifies known CVE vulnerability exposure and misconfigurations across server environments.
Reduced Operational Overhead
Automation eliminates manual tracking and repetitive tasks, allowing teams to focus on remediation instead of data collection.
Consistent Vulnerability Security Visibility
Dashboards provide real-time insight into risk trends, remediation status, and overall vulnerability management security posture.
Faster Vulnerability Remediation
Risk-based prioritization enables teams to address the most critical security vulnerability issues first.
Audit-Ready Reporting
Reports support internal reviews and compliance workflows without additional tooling or services.
Open Source Vulnerability Management Visibility
Open source vulnerability management highlights known risks across commonly used components, helping teams track exposure and maintain clear visibility with minimal effort.


Six Simple Steps to Strengthen Server Vulnerability Security

Connect Your Environment
Get started by securely connecting your server environment to SeqOps. This step establishes visibility into assets and prepares the platform for automated vulnerability management security scanning.

Initialize Security Baseline
SeqOps configures an initial security baseline by analyzing system metadata and configurations. This creates a clear starting point for ongoing vulnerability management security.

Provide Configuration Context
Answer a few guided questions to help the platform better understand your environment. This context improves scan accuracy and supports more relevant vulnerability detection.

Automated Scanning Begins
SeqOps continuously scans servers to identify known CVE vulnerability exposure and configuration risks, maintaining consistent vulnerability management security over time.

Clear and Actionable Findings
Findings are presented in a structured, easy-to-understand format. Issues are prioritized by risk and impact, enabling faster and more confident remediation decisions.

Strengthen Security Posture
Use remediation insights and tracking workflows to reduce exposure and improve vulnerability management security across your server infrastructure.
Server Security with Automated Vulnerability Management Security and Reporting
Effective server security requires a continuous and structured approach. SeqOps delivers a product-led vulnerability management security platform that automatically identifies security gaps and maintains visibility into server risk through ongoing scanning and reporting.
The platform automatically scans for known vulnerabilities and configuration problems, giving you clear security results without you having to do anything. Security vulnerability management solutions help make quick decisions about how to fix problems by keeping an eye on things all the time.
SeqOps also keeps track of changes to configurations and progress on fixing problems to make vulnerability management security stronger over time. Automated reporting gives you a clear picture of your security posture, which helps you keep your protection up as your server environments change.
Adaptive Vulnerability Management Security for Server Environments
SeqOps delivers a product-led vulnerability management security platform designed to maintain consistent visibility across server environments. Automated scanning evaluates configurations and known vulnerability exposure, ensuring security gaps are identified without manual assessments.
The platform combines continuous scanning and automated analysis to surface actionable findings. Results are organized to support faster decision-making and effective security vulnerability remediation through a clear, repeatable workflow.
As environments evolve, SeqOps continuously updates findings and remediation status to maintain vulnerability management security over time. Automated monitoring and reporting help keep security posture aligned as infrastructure changes.

Pricing Plans for SeqOps Server Security
SeqOps doesn’t just protect; it empowers. Its comprehensive reporting transforms raw data into actionable insights, helping administrators:
Basic
Per month price:
30 Days
Scanning Frequency
What you get:
- Monthly reporting
- Vulnerability detection
Advanced
Per month price:
30 Days
Scanning Frequency
What you get:
- Monthly reporting
- Vulnerability detection
Enterprise
Custom Quote
Full security and tailored to your needs
30 Days
Scanning Frequency
What you get:
- Managed Detection
- GDPR and NIST Reporting
- Threat alerts and attempt block
- Daily scans and reporting
Related Posts
- /
Data breaches now cost businesses an average of $4.45 million per incident, a record high according to the...
- /
Did you know that over 60% of data breaches result from unpatched security flaws that organizations knew about...
- /
A staggering 68% of businesses experience a significant security incident within their first year of operation. This alarming...
Frequently Asked Questions
What is vulnerability management security?
Vulnerability management security is a SaaS-based process that runs all the time and finds, ranks, and keeps track of security holes in server environments. SeqOps makes it easier to find and fix problems by scanning constantly and using structured workflows.
Why do I need vulnerability management security?
Vulnerability management security helps maintain consistent visibility into security risk as systems change. Automated scanning and prioritization reduce manual effort and support faster remediation decisions before issues impact operations.
What does vulnerability scanning mean in vulnerability management security?
Vulnerability scanning is the automated discovery of known CVE exposure and configuration flaws. In vulnerability management security, scans run all the time to make sure that security findings are up to date and can be acted on.
What kind of support does SeqOps provide?
The SeqOps platform offers in-product guidance, insights on how to fix problems, and status tracking. Vulnerability management security workflows and reports help teams understand what they find and how far they’ve come without needing outside help.
How do I know if a vulnerability is patched?
Vulnerability management security keeps track of the status of fixes on its own. The platform updates the vulnerability state and shows closure in reporting dashboards after it finds changes during later scans.
Can SeqOps work with developers on patching vulnerabilities?
SeqOps does not offer hands-on help with fixing problems. Vulnerability management security helps teams fix problems faster by giving them clear results, setting priorities, and keeping track of fixes on the platform.

Ready to Improve How You Manage Security?
Discover how the SeqOps platform helps your business work more efficiently while keeping your organization secure now and as you grow.



